Achieve a secure and robust IT foundation with our
Three Step Complete IT Support Solution



We Become Your IT Department
We Make Cybersecurity The Priority
We Develop Lasting Business Relationships
Do these IT Problems Sound Familiar?
Struggling with Unreliable IT Services..
Frequent downtime and technical issues disrupting your operations? We provide reliable IT services to ensure your systems run smoothly.
Concerned About Cybersecurity Threats...
Worried about data breaches and cyber attacks? Our cybersecurity-focused IT services protect your business from evolving threats.
Lacking In-House IT Support Capabilities and Expertise...
Don't have the personnel or resources to maintain a full IT services department? We become your dedicated IT team.
We're Here to Set the Record Straight...
You Deserve a Reliable Partner in IT Services and Security

At DeVeera, we believe in building strong partnerships with our clients. We immerse ourselves in your business to understand your unique needs and challenges. By aligning our IT services with your objectives, we ensure that technology becomes an enabler for your success.
Our team takes a proactive approach, continuously monitoring and optimizing your IT services infrastructure. We focus on preventative maintenance and strategic planning, so you can avoid issues before they arise. With our comprehensive IT services, you can concentrate on your core business while we handle the technology.

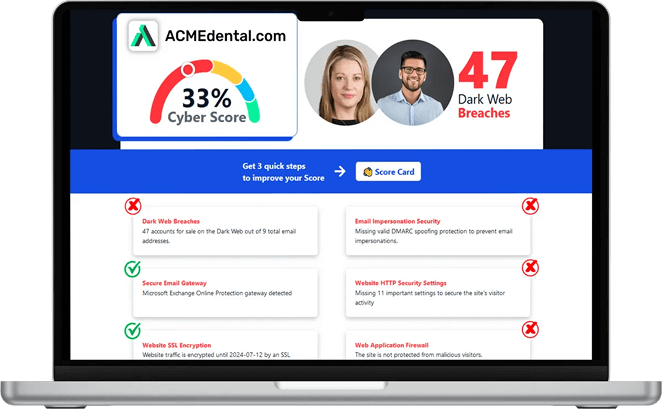
Think you're secure? Get your Cyber Security Score!
Get it in 30 seconds!
Here is How We Do it:
Proactive IT Services
We continuously monitor your IT services systems to detect and resolve issues before they impact your business. This proactive approach minimizes downtime and keeps your operations running smoothly.
Customized Solutions
We tailor our IT services to fit your specific industry and business needs. By providing customized solutions, we enhance efficiency and support your operational goals.
Expert Cybersecurity
Our cybersecurity experts implement robust IT services measures to protect your data and systems. We stay ahead of emerging threats to ensure your business remains secure.
Dedicated Support
Our team is always available to provide prompt and professional IT services support. We value strong relationships and are committed to your satisfaction.
Ready for Better IT Services?
Don't let IT services challenges hold your business back. Partner with DeVeera to experience seamless IT services tailored to your needs. Our team is ready to provide the expertise and support that will drive your business forward.
Give us a call at (831) 243-3452 or complete the form, and we will get in touch with you to set up an introductory phone call.
What Happens Next?
Fill in our quick form
We'll schedule an introductory phone call
We'll tale the time to listen and plan the next steps
What Makes Us Different?
DeVeera helps Monterey Bay businesses achieve secure and optimized IT networks.
Experience Matters
With over 20 years in the industry, DeVeera has the expertise to handle all your IT needs. Our seasoned team understands the challenges businesses face and delivers effective solutions.
Industry Expertise
We specialize in serving a variety of industries, including agriculture, healthcare, and professional services. Our knowledge of industry-specific requirements allows us to provide targeted IT support.
Full-Service Provider
From managed IT services to software development and compliance, we offer a comprehensive suite of services. This means you have a single, reliable partner for all your technology needs.
Core Values
Our commitment to respect, integrity and professionalism guides everything we do. These core values ensure we deliver exceptional service and build long lasting relationships with our clients.
Global Reach
Though we're based in California, we serve clients nationally and globally. No matter where your business is located, DeVeera is equipped to support your IT services needs.
Passionate Team
Our team loves what they do. This passion translates into exceptional service and a proactive approach to solving your IT challenges. We make IT easy—and even enjoyable.
Stop Managing Your IT Internally
Managed IT
Managed IT services provide proactive management of your IT infrastructure to enhance efficiency and reduce costs.
With our managed IT services, you gain access to a team of experts who monitor and maintain your systems around the clock. We prevent issues before they arise, ensuring optimal performance and security. This allows you to focus on your core business while we handle the complexities of IT management.


DeVeera Guardian Shield
Cybersecurity IT services protect your business from threats, ensuring data integrity and maintaining trust with clients and partners.
With our cybersecurity IT services, we implement advanced security measures to safeguard your IT infrastructure from cyber attacks and data breaches. Our team continuously monitors for threats and vulnerabilities, providing proactive defense to keep your business operations secure and efficient. By protecting your critical information, we help you maintain compliance, avoid costly disruptions, and build confidence with your clients and partners.
IT Projects
IT project services deliver specialized solutions for your unique business challenges and technological initiatives.
Our IT project services provide the expertise to plan, execute, and manage your technology projects effectively. Whether it's system upgrades, migrations, or custom software development, we ensure projects are completed on time and within budget. We align solutions with your strategic goals to drive growth and innovation.

Join Our Growing Community of Smart Business Leaders by Signing Up for Our Free Email List
Gain Access to Our Exclusive Email Distribution List and Learn How a Carefully Developed IT Strategy Can Help Your Organization Operation More Efficiently
Keeping your IT ahead of the curve is a full-time job (and then some). That’s why we make it a point to educate our clients on the principles of IT before they make a big decision.
Our email list covers a range of key topics at the intersection of IT strategy and business management, explaining:
The many overlooked ways that properly managed IT can contribute to business growth and development.
What a contemporary approach to cybersecurity should address.
How IT can increase productivity, help you automate certain tasks, and most importantly, reduce your overhead.

FAQs
What are your service areas?
DeVeera is located in Monterey, CA, and we service business onsite throughout California. However, with most businesses now being cloud-based, in many cases, we are able to provide remote support solutions to businesses nationwide.
What happens when I call for support?
We pride ourselves on providing excellent customer service. When you call us, you can expect a rapid, courteous response from a real person. We understand how important it is to be able to speak to someone directly when you have questions or concerns, and we will do everything we can to address your needs.
Can my employees reach out for support directly, or just me?
Your employees will be able to reach out to us directly. We'll be able to help resolve the issue quickly and efficiently.
Can you help with cybersecurity?
Of course! Cybersecurity and compliance are the cornerstone to any modern IT strategy. We include cybersecurity measures in all of our packages.
